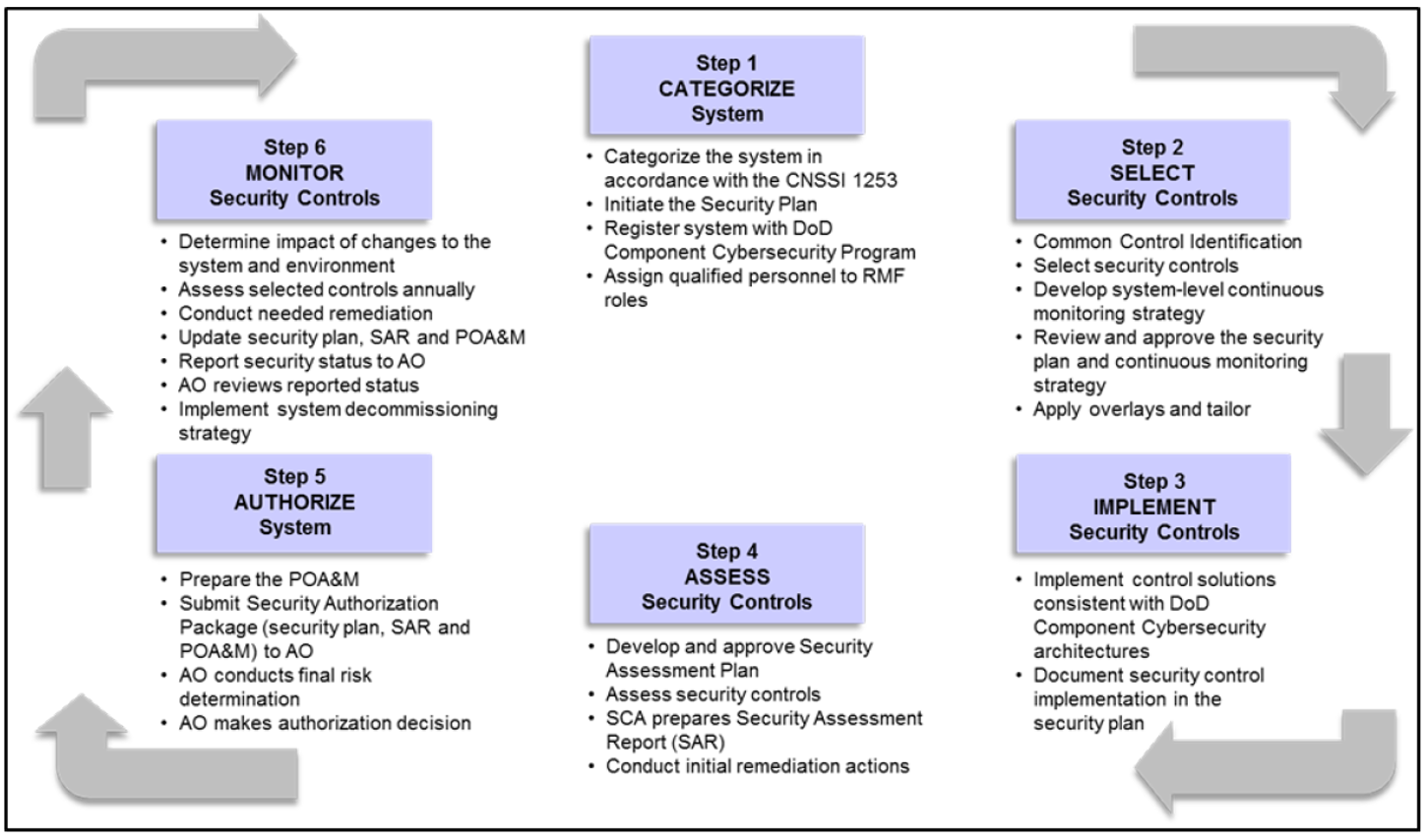
Cybersecurity Risk Management Framework (RMF)
A framework that brings a risk-based, full-lifecycle approach to the implementation of cybersecurity. RMF supports integration of cybersecurity in the systems design process, resulting in a more trustworthy system that can dependably operate in the face of a capable cyber adversary. RMF emphasizes
integrating cybersecurity activities into existing processes including requirements, SSE, program protection planning, trusted systems and networks analysis, developmental and operational test and evaluation, financial management and cost estimating, and sustainment and disposal.
PMs need to ensure cybersecurity risks are actively managed consistent with system performance requirements, and are acceptable to the Service-designated Authorizing Officials (AO), who provide the system Authorization to Operate (ATO). Close coordination between the PM and AO is critical to the management of cybersecurity risks throughout the entire acquisition process.
Key Tenets:
- Cybersecurity is risk-based, mission-driven, and addressed early and continually.
- Cybersecurity requirements are treated like other system requirements.
- System security architecture and data flows are developed early, and are continuously updated throughout the system lifecycle as the system and environment (including threats) change, to maintain the desired security posture based on risk assessments and mitigations.
- Cybersecurity is implemented to increase a system’s capability to protect, detect, react, and restore, even when under attack from an adversary.
- A modular, open systems approach is used to implement system and security architectures that support the rapid evolution of countermeasures to emerging threats and vulnerabilities.
- Cybersecurity risk assessments are conducted early and often, and integrated with other risk management activities.
- As the system matures and security controls are selected, implemented, assessed, and monitored, the PM collaborates with the authorizing official (AO), the individual responsible for ensuring the cybersecurity risk posture of the system is managed and maintained during operations, to ensure the continued alignment of cybersecurity in the technical baselines, system security architecture, data flows, and design.
- Reciprocity is used where possible through sharing and reuse of test and evaluation products i.e., “test once and use by all.”
The six steps of the RMF process are represented in the diagram below.
The following three security objectives should be considered when trying to balance specific cybersecurity requirements with the other requirements that apply to the system:
- Confidentiality – The property that information is not disclosed to system entities (users, processes, devices) unless they have been authorized to access the information. NIST SP 800.53: Preserving authorized restrictions on information access and disclosure, including means for protecting personal privacy and proprietary information.
- Integrity – The property whereby an entity has not been modified in an unauthorized manner. NIST SP 800-53: Guarding against improper information modification or destruction, and includes ensuring information non-repudiation and authenticity.
- Availability – The property of being accessible and useable upon demand by an
authorized entity. NIST 800-53: Ensuring timely and reliable access to and use of
information.
References